My journey to OSWE
Previously on “Patrick does OffSec Courses”
Summary
It’s been a while. And just yesterday I did pass my OSWE exam first try. So I thought, why not share my two cents on how the course compares to OSEP, which I did pass this January.
Again I cannot talk about details regarding the exam, as this would violate Terms & Conditions, but I think I can give a good insight nontheless.
Preperation Phase
Since I did the OSEP, OffSec changed their prices a bit. Also you don’t have the choice of having a 30, 60 or 90 days lab anymore. It is now either 90 days lab or what they call “Learn One”, which will give you access to a course of your choice for one year. Two exam attempts are also included in this subscription.
I went for the “normal” 90 days lab access with one exam attempt, as I was quite confident I can make it first try. As a pentester doing webapp pentests since 2017 I thought this should be sufficient enough. And to be fair, my time management still is quite good. Having experience with running through the OSEP course material I dived into the course head first expecting a lot of pain and suffering.
Boy was this a surprise to me. Guess what, I had fun. “Fun?”, I hear you asking. Let me explain.
I love learning new things. That is what I am having fun with the most. And although I am a professional pentester for a decent amount of time now, the course material was totally new to me. As this course is mostly about Source Code review and white box pentesting it does not compare to webapp pentests, which are black/grey box pentests whatsoever.
So as a result my learning curve was really steep, which was the reason for me having a lot of fun. Sure, your eyes can get sour reading through thousands of lines of code looking for one specific vulnerability.
But it is really rewarding finding a complex blind SQL Injection in the source code when you know you would have never been able to find this in a black box test. Or as another example, finding a logic bug that lets you calculate a token to reset someones password will make you feel like a god.
And as OffSec is using real world examples of Open Source code this blew my mind even more. To be fair, I never was that guy looking into source code much. But the time you realise those are real vulnerabilities in real apps which are deployed out there…
As a conclusion to the preperation phase - OSWE was way more fun in this phase than OSEP. And just to be completely transparent, I did finish the course material in about 25 days doing a workload of about 40 hours a week.
Not playing the waiting game this time
I learned from my previous mistakes regarding exam schedule. So let me illustrate my timeline in this section. I was starting my lab time from 1st of October which results in the lab time ending 90 days later, which is the 30th of December 2022.
If you have read my post about my OSEP journey you might remember this advice:
Schedule your exam right after your lab time ends
I did not follow my advice, again. But this time for better. To be fair, I did follow my advice at first. Right after I registered for the course my first action was to schedule my exam right before christmas between the 21st and 23rd of December.
But then I felt like I do not want to wait until the end of December to take the exam, while I was already fully prepared and ready to hit it. So I rescheduled my exam to be from the 14th to the 16th of November. This was the best decision I could have made.
In the meantime I did still practise on a daily basis. There are some good resources you can train with other than OffSec’s course material. One good example is the TUDO-App.
So still I had to wait for about 3 weeks but this was not as nerve-wrecking as waiting until January again.
The Exam
Now comes the serious part, maybe? Well, at least I could sleep “okay” the day before the exam. Not good, but okay. I was way more confident than I was before taking the OSEP exam. So as a result I was not as nervous.
Again, I was scheduled for a morning exam start at 9 am. Around 8 am’ish I was sitting at my desk, preparing the last bits and pieces to have a really good start into the exam. Things like shortcuts to remote desktop connections, displaying all the notes already, having skeleton scripts readily available and such.
5 minutes early I logged into the proctoring session and started verifying my identity and all the things you will have to do for that proctored sessions. And then the exam E-Mail was coming in. I connected to the VPN and there we are. We are in an OffSec exam again 😄.
This time I took it slower than with OSEP. I read the objectives multiple times and started taking structured notes of what I am supposed to do, before even connecting to one of the machines. This was good to calm down a bit the adrenalin rush you will inevitably have starting the exam.
Then I connected to one target and suddenly my mood changed - a lot. Just for you guys to understand the structure of the exam better. You will have 2 targets you have to do “Authentication Bypass” and “Remote Code Execution” on. This sums up to 4 flags in total. To be able to debug and read the source code you will be given 2 identical debugging machines that you can connect to via remote desktop protocol. And a kali machine you can connect to via ssh to test you payloads against the final targets. You are not allowed to copy the source code of the application to your host system or to remotely mount it using sshfs or other tools. So for analyzing the source code you are bound to that specific remote desktop connections.
And this was the crucial part. The connection to that lab environment was bad. Really bad. It was lagging and not working for me in any way. I tried opening a terminal and after it opened I issued the command ls -la. This action took around 10 minutes. How am I supposed to do an exam with this environment. That is impossible! So I panicked. Just to mention, I am on a Fibre-to-the-Home connection giving me 400 MBit connection speed #weird-flex. This should be more than sufficient.
So immediately I was telling the proctor in the live chat that I do have connection issues. He dispatched my problem to the technical staff of OffSec and they provided a solution. I was changing MTU on my connection interface and they did a thing on their end. In addition, I was reducing screen resolution and bitrate of the remote connection and then it went smooth’ish. At least smooth enough to be able to effectively read source code. Let me tell you that this was not the last time I had to chat with the proctor. Their support quality increased drastically since January.
Now I was really “starting” the exam and was totally hyped. Jump cut to 10 hours later. See me sitting on my couch contemplating on returning to my desk or just quitting the exam right away. Yeah, it happened again. What a shame. I was hitting the first application for 10 hours straight not progressing a single bit. I was hunting down rabbit holes, wasting a ton of time and being all sad about not pwning the machines, like I imagined I would.
As a lesson to everyone, especially myself, those exams are not easy. And they are also not supposed to be. Don’t ask me what I thought will happen. I must have thought I can just beat the exam straight away. But this time I regained confidence a lot quicker. I took a longer break (around 1 hour) and then returned to my desk with a fresh and strong attitude.
Jump cut again to 1 hour later. See me writing a complex python script chaining 4 steps together, combining two different non-trivial vulnerabilities to finally exfiltrate the first of 4 flags. What a reliev. I can do it. I am worth passing that exam.
What happened? I read throught the source code once again and suddenly everything started to fall into place. What looked like a neglectable irregularity to me first, turned out to be the exact vulnerability I should use to get my exploit chain started. So now it was just a matter of coding a good exploit script to get me started on that machine. At that time it was 8:15 pm, so I was almost 12h into the exam. Just another 5 hours later (1:20 am second exam day) I was done with that first machine. And let me tell you, that feeling is not to be described with words.
I decided to go to bed and get some sleep to regain strength for the second machine to be hacked the next day. But unfortunately I could not rest as desired. I took a quick sneak peek of the source code on the second machine before I went to bed. I should not have done that. Because this night my mind was already solving the complete app with all its steps. At least this is what it felt like. I was trying to fall asleep with techniques like “Progressive Muscle Relaxation”, “Breath Exercises” and comparable, but I did not manage to get good sleep. Finally my body gave up and I fell asleep for what felt like 5 minutes to me.
The next morning at 7 am I woke up and decided to slowly start into the second day of hacking. Mentally I was preparing for another 17 hours of stressfully hitting walls over and over again. So I started slowly by grabbing a coffee, hugging my kids a lot, resting my mind trying not to think about what will follow next.
But eventually I returned to my desk at 9 am to look into the second machine. And to my surprise my mind did solve the complete machine while I was “sleeping”. This is no joke. I returned to the source code immediately seeing what was off. It was 1,5 hours later that I bypassed the authentication and had a working script. And finally I was surprised again. Not even did I start to have fun doing an OffSec exam, but after running down a rabbit hole for around 1 hour I then managed to get out of it and solve the box quite fast at 2 pm on the second day.
I was done - I got it - 100/100 points. Is that real? Am I real? Am I maybe still sleeping? No, I was done and the even better part about this is, I had fun at the end.
The Aftermath
And with this feeling I started to write my report right away. Because why not? I do still have access to the machines, so I can make sure I do have all the screenshots I will need for my report. And if I don’t have them, I could still connect to the machine and get them if needed.
As you say in englisch “Business before pleasure”. Writing the report not felt like business to me. Although as a pentester this normally is business, I felt a bigger and bigger relieve after every single word I typed into that report.
At 5:30 pm on that second exam day, around 32 hours into the exam, I pressed the “End Exam” button in my control panel and called it quits. I had everything ready to pass the exam. I went downstairs and did not think about the exam until the next day. This rest period was really good. I could have read through my report over and over again, but that would not have changed anything. At this time I was already zoning out. My body was claiming what it was missing the last 36 hours.
So the next morning I returned to the report for the final finishing touches. It turned out to be another 5 hours shift until my report was all polished and shiny and nice. But it was well worth it going through it again, rewriting some sections and editing some screenshots.
Finally the report was all done and I submitted it to OffSec through their upload form. This felt strange, like every time I did it. But this is final. No possibility of changing anything.
The next day I was casually browsing the Offensive Security Portal page, where you do study the course material and I was thinking to myself: “What happens if I click the ’exam’ tab?”. To clarify, this tab is meant to schedule your exam. And I was curious which page it will show, now that I already took my one exam attempt that is included in the course fee.
And to my surprise I saw this:
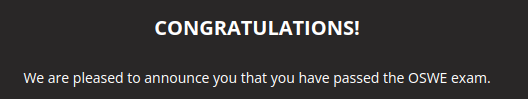
I immediately went to the community discord, because I did not trust that output. I thought this has to be some template output until they check on my exam results. I mean, it was not yet 24 hours after I handed in my report. This could not be real, can it?
The community discord quickly confirmed that this in fact was real. I did pass, even without being notified by mail yet. But I did pass. This felt unreal, but I was happy. Not as much as I would have imagined, but I was happy. But to be fair, after having such a good time at that course and the second half of the exam I was already confident I would pass 😉. Although it was not as glamorous as it was when I got notified that I passed OSEP, it still felt pretty awesome.
Shortly after this the E-Mail arrived telling me that I passed. So it was “official” official. I passed.
Conclusion
So how does it compare to OSEP? Well, maybe my mind and attitude changed or it was just the topic, which was easier for me to digest. But to summarize: I had a lot more fun doing OSWE compared to OSEP. I felt good and confident while doing it. I had so much fun during the course material that I had to force myself to get away from the computer and not go through the material in one run.
What up next?
Well, most of you might have guessed already that I am after becoming a OSCE³. That means I will do the Offensive Security Windows User Mode Exploit Development (OSED) course next. At least this is my plan. I am really afraid of this course, as this is and has not been any of my business yet. So I consider buying the “Learn One” subscription for this one. Because this will give me way more time to train for it and also having 2 exam attempts can come in handy. Also the price difference between those two subscriptions is not that much, to be fair. So stick around and you may find out how it feels like to become an OSED.
As always I hope you enjoyed reading the insights of becoming OffSec certified.
Cheers, Patrick