I hacked the german armed forces, and all I got …
A Vulnerability Disclosure Policy, short term is VDP, is a good thing in my opinion. Hackers get motivated by them to uncover vulnerabilities lurking in your network. As a reward often things like a cup or a t-shirt are gifted to the researcher.
This blog post is about, how I hacked the german armed forces and got more than a lousy t-shirt.
Not long ago an old friend of mine brought to my attention that the german armed forces do have a Vulnerability Disclosure Policy.
Vulnerability Disclosure Policy
What is a Vulnerability Disclosure Policy, you may be thinking to yourself. A VDP is a wildcard for hackers to uncover vulnerablities within the targets network without being persued and fined. So this sounds to good to be true? Trust me, it is true! The only restriction is that you are supposed to responsibly disclose the vulnerability to your target.
Motivation
Some of you might think - “That is a free pentest, isn’t it?” - and yes, that might be true to some extend. Nonetheless the researcher has to be lured into testing your network, right? So how do you do this as a company? Next to fame and recognition, often what you get as a security researcher is some kind of fancy cup or t-shirt. Well, I tell you that I have enough T-Shirts in my closer already and I do have so many cups that I couldn’t make enough coffee to fill all of them.

Well, fortunately the german armed forces are not the dutch government and will provide a way cooler reward - the VDPBw-Coin.
So this is motivation right there, isn’t it?
Procedure
So how do you proceed “hacking the german armed forces”? In contrary to a classic penetration test you will first need to get a lot of information about your target before you can start hacking.
In a classic penetration test you will be provided with a “scope” - what are you supposed to attack - and a goal - what are you supposed to accomplish.
But compared to this the german armed forces will not provide you with a list of systems they want you to attack. Also they do not provide a goal to accomplish.
This you will have to find out by yourself.
Reconnaissance
Like with every good military company you will need to do some reconnaissance first. Funny how this compares to the military, right?
Besides ressources like the RIPE-Database or Shodan some attack techniques like Subdomain-Bruteforcing and analysing web certificates will apply.
The goal of recon is to find as much domains and subdomains owned by the target as humanly possible. This will be the crucial foundation of the subsequent attacks.
Network analysis
Let’s say you harvested enough domains and subdomains you are ready for attacking a little more “actively”. While doing the network analysis you will harvest information about active services exposed to the internet. You will also, for example, screenshot the contents of web pages in an automated fashion.
This is how you specialize your attacks further down the road. Guessing valid paths and files within a web page is also a fundamental action in this phase.
The finding
If you then find anything interesting (like an old looking page, a typical app with known vulnerabilities, error or debug information pages) you will proceed more manually.
A finding is only then a finding if you can proof and reproduce it. At least this is how I act on reporting findings. In this case it means, that you are supposed to confirm the finding manually.
Often times it then happens, that you will discover an even more critical finding, than you were assuming at first.
I will not go into any detail on what I have found while analysing the german armed forces network for an obvious reason. But trust me if I tell you that I was able to identify vulnerabilities from a low rated information disclosure (debug information or stack traces) to a high critical SQL-injection vulnerability (direct interaction with the underlying database) 😃.
The next part is the most crucial one.
Reporting
So for the targetto be able to reproduce and fix the identified vulnerability the way you report the vulnerability is crucial.
For this to be as easy as possible for the security researcher, the german armed forces offer a template. This templates includes topics like:
- Title of the vulnerability
- Type of the vulnerability
- Non-technical Summary
- What is the subject of the vulnerability (webapp XY)
- Technical details
- Proof-of-Concept (best would be a clickable link)
- And most important: A possible mitigation
In general this is almost identical to how I would write a finding in a classic penetration test report.
This information you will send to an email address they provide. Also be sure to encrypt (PGP) it properly. Shortly after an automated mail response will confirm they got your report.
Now we play the waiting game.
Success!
How do you get notified that they recognize your finding? Short answer: You don’t.
If you follow the “Cyber- und Informationsraum Bundeswehr” - short term: cirbw - on Twitter though, you might catch your name in one of those tweets with the hashtag #VDP.
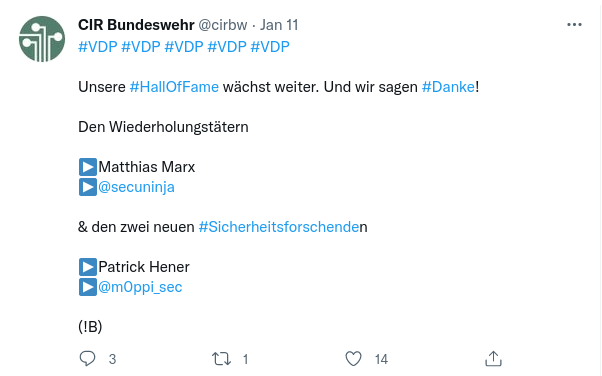
Or you just take a look into the hall of fame of the german armed forces.
Getting awarded
If you bring at least three vulnerabilities to their attention, which get recognised you will be awarded the VDPBw-Coin, which they send you via mail.
Looks nice, right?

Conclusion
Was it worth it to participate? Absolutely yes. This was a lot of fun.
Would I have done it for a t-shirt or a fancy cup Sure enough. Even without getting a reward. This is a matter of honour!
Thanks for reading.
Cheers, Patrick